Step 6: The second way to enter a static IP address is through CLI, this is the most efficient way to program the computers in CISCO PACKET TRACER because it is the most accurate way of working in real equipment. To do this, enter the global user mode and place the following commands: Interface fastethernet 0/0. Ip address 10.0.0.1 255.255.255.0. Useful commands to be used in conjunction with the packet-tracer is “clear conn” and “clear xlate” to clear connection table and NAT-table. NOTE: You will obviously kill all IP-sessions running through the appliance using the clear-commands.
Cisco ASA includes a very nice feature since the 7.2(1)-release; packet-tracer.
In short, you can inject and trace a packet as it progresses through the security features of the Cisco ASA appliance and quickly determine wether or not the packet will pass.
I often use it to verify traffic passing through firewall rules, NAT-rules and VPN, but its uses is not limited to these three common troubleshooting steps.
Command structure
packet-tracer input <source interface> <protocol> <source IP> <source port> <destination IP> <destination port> [detailed]
Useful commands to be used in conjunction with the packet-tracer is “clear conn” and “clear xlate” to clear connection table and NAT-table.
- NOTE: You will obviously kill all IP-sessions running through the appliance using the clear-commands. So use it at your own risk and don’t blame me if your users comes running after you wielding pitch forks and torches. ,)
Example
Following is an example of a packet-trace to a web-server through a VPN-tunnel, without the “detailed”-option.
My comments in red.
Packet Tracer Command Prompt Clear Screen
CiscoASA# packet-tracer input inside tcp 10.20.30.40 54444 10.50.60.70 http
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: FLOW-LOOKUP
Subtype:
Result: ALLOW
Config:
Additional Information:
Found no matching flow, creating a new flow
Phase: 3
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 0.0.0.0 0.0.0.0 outside
Phase: 4
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group ACL-inside-in in interface inside
access-list ACL001f-inside-in extended permit ip any any
Additional Information:
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect http
service-policy global_policy global
Additional Information:
Phase: 7
Type: NAT-EXEMPT
Subtype:
Result: ALLOW
Config:
nat-control
match ip inside 10.20.30.0 255.255.255.0 outside 10.40.50.0 255.255.255.0
NAT exempt
translate_hits = 51480, untranslate_hits = 854212
Additional Information:
THE TRAFFIC IS NOT NATED, EVEN THOUGH PHASE 8/9 RESULTS YIELDS RESULT “ALLOW”.
Phase: 8
Type: NAT
Subtype: host-limits
Result: ALLOW
Config:
nat (inside) 1 access-list inside_nat_outbound
nat-control
match ip inside 10.20.30.0 255.255.255.0 outside host 10.2.2.10
dynamic translation to pool 1 (200.200.200.200 [Interface PAT])
translate_hits = 0, untranslate_hits = 0
Additional Information:
Phase: 9
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside) 1 10.20.30.0 255.255.255.0
nat-control
match ip inside 10.20.30.0 255.255.255.0 outside any
dynamic translation to pool 1 (200.200.200.200 [Interface PAT])
translate_hits = 3205631, untranslate_hits = 383007
Additional Information:
Packet Tracer Command Line
Phase: 10
Type: VPN
Subtype: encrypt
Result: ALLOW
Config:
Additional Information: TRAFFIC MATCHES VPN AND WILL BE ENCRYPTED
Phase: 11
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Phase: 12
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 13
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 10948889, packet dispatched to next module
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: allow FINAL ACTION IS ALLOW WHICH MEANS THE PACKET IS NOT STOPPED IN CONFIGURATION AND WILL BE PASSED ON.
If I try to run the same command again, we will see it matches an existing flow in phase 2 and promptly passed on.
CiscoASA# packet-tracer input inside tcp 10.20.30.40 54444 10.50.60.70 http
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: FLOW-LOOKUP
Subtype:
Result: ALLOW
Config:
Additional Information:
Found flow with id 10953078, using existing flow
Result:
input-interface: inside
input-status: up
input-line-status: up
Action: allow
Packet tracer via ASDM / GUI
You can also find the packet-tracer is ASDM via “Tools > Packet Tracer”:
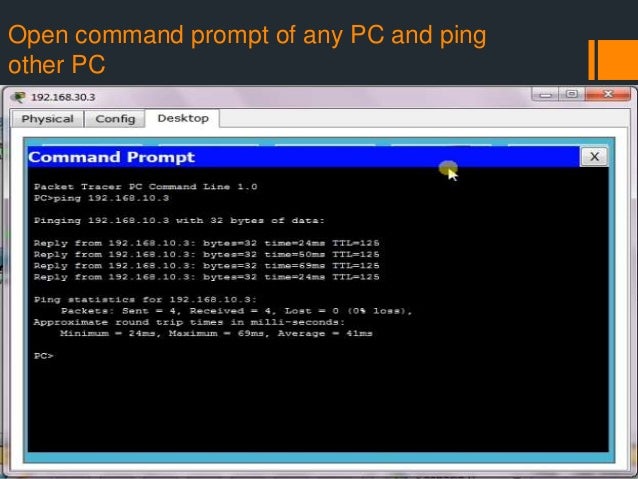
9.2.3.3 Packet Tracer – Using the Ping Command Answers
Packet Tracer Command Prompt Ping
Packet Tracer – Using the Ping Command (Answers Version)
Answers Note: Red font color or gray highlights indicate text that appears in the Answers copy only.
Topology
Objectives
Use the ping command to identify an incorrect configuration on a PC.
Background / Scenario
A small business owner learns that some users are unable to access a website. All PCs are configured with static IP addressing. Use the ping command to identify the issue.
Step 1: Verify connectivity.
Access the Desktop tab > Web Browser of each PC and enter the URL www.cisco.pka. Identify any PCs that are not connecting to the web server.
Note: All of the devices require time to complete the boot process. Please allow up to one minute before receiving a web response.
Which PCs are unable to connect to the web server?_____________ PC2
Step 2: Ping the web server from PC2.
- On PC2, access the Command Prompt from the Desktop tab.
- Type ping www.cisco.pka.
Did the ping return a reply? What is the IP address displayed in the reply, if any?____________________________________________________________________________________
There was no reply. No IP address was displayed in the message.
Step 3: Ping the web server from PC1.
- On PC1, access the Command Prompt from the Desktop tab.
- Type ping www.cisco.pka.
- Did the ping return a reply? What is the IP address returned, if any?____________________________________________________________________________________
Reply was returned with 192.15.2.10 as the IP address for www.cisco.pka.
Step 4: Ping the IP address of the web server from PC2.
- On PC2, access the Command Prompt from the Desktop tab.
- Attempt to reach the IP address of the web server with the command ping 192.15.2.10.
- Did the ping return a reply? If so, then PC2 is able to reach the web server via IP address, but not domain name. This could indicate a problem with the DNS server configuration on PC2.

Step 5: Compare the DNS server information on PC2 with other PCs on the local network.
Ssh Command Prompt Packet Tracer
- Access the Command Prompt of PC1.
- Using the command ipconfig /all, examine the DNS server configuration on PC1.
- Access the Command Prompt of PC2.
- Using the command ipconfig /all, examine the DNS server configuration on PC2. Do the two configurations match?
Step 6: Make any necessary configuration changes on PC2.
Packet Tracer Commands List
- Navigate to the Desktop tab of PC2, make any necessary configuration changes in IP Configuration.
- Using the Web Browser within the Desktop tab, connect to www.cisco.pka to verify that the configuration changes resolved the problem.
- Click the Check Results button at the bottom of this instruction window to check your work.